Microsoft Endpoint Manager Configuration Manager (MEMCM / SCCM) and Microsoft Intune use Detection Rules to determine the presence of Applications & Win32 Apps. The detection rules ensure that application installations only begin to run if the application is not already installed on the device. This article will serve as an informative guide and give you a clear understanding of how to create an updated custom detection script for each new version of Microsoft Azure Information Protection using PowerShell.
How to Create a Custom Detection Script for Microsoft Azure Information Protection
Microsoft Azure Information Protection (File Detection Method)
-
Install the version of Microsoft Azure Information Protection you want to deploy on a test box or VM
- Check out the following posts for further details
- Open Windows PowerShell ISE by Right-Clicking on Windows PowerShell ISE and selecting Run as Administrator
- Copy the following code into the Windows PowerShell ISE
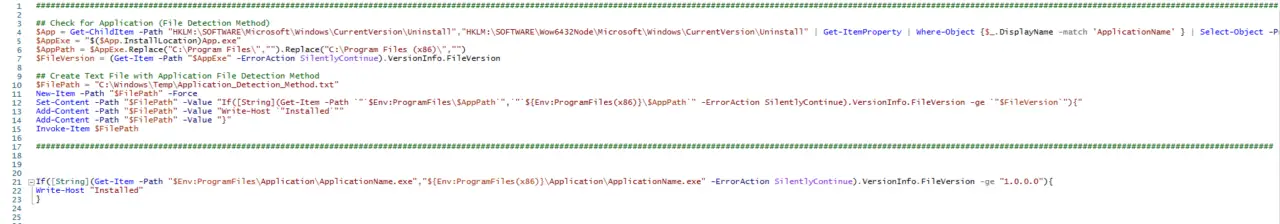
## Check for Microsoft Azure Information Protection (File Detection Method)
$AzInfoProtectionExe = (Get-ChildItem -Path "C:\Program Files\Microsoft Azure Information Protection\MSIP.Viewer.exe","C:\Program Files (x86)\Microsoft Azure Information Protection\MSIP.Viewer.exe" -ErrorAction SilentlyContinue)
$AzInfoProtectionExe.FullName
$AzInfoProtectionPath = $($AzInfoProtectionExe.FullName).Replace("C:\Program Files\","").Replace("C:\Program Files (x86)\","")
$FileVersion = (Get-Item -Path "$($AzInfoProtectionExe.FullName)" -ErrorAction SilentlyContinue).VersionInfo.FileVersion
## Create Text File with Microsoft Azure Information Protection File Detection Method
$FilePath = "C:\Windows\Temp\Azure_Information_Protection_Detection_Method.txt"
New-Item -Path "$FilePath" -Force
Set-Content -Path "$FilePath" -Value "If([String](Get-Item -Path `"`$Env:ProgramFiles\$AzInfoProtectionPath`",`"`${Env:ProgramFiles(x86)}\$AzInfoProtectionPath`" -ErrorAction SilentlyContinue).VersionInfo.FileVersion -ge `"$FileVersion`"){"
Add-Content -Path "$FilePath" -Value "Write-Host `"Installed`""
Add-Content -Path "$FilePath" -Value "Exit 0"
Add-Content -Path "$FilePath" -Value "}"
Add-Content -Path "$FilePath" -Value "else {"
Add-Content -Path "$FilePath" -Value "Exit 1"
Add-Content -Path "$FilePath" -Value "}"
Invoke-Item $FilePath
- Click Run Script (F5)
- A text file will open with the Microsoft Azure Information Protection Detection Method script required to detect the current version of Microsoft Azure Information Protection that is installed on the device you are running the script from.
Example:
If([String](Get-Item -Path "$Env:ProgramFiles\Microsoft Azure Information Protection\MSIP.Viewer.exe","${Env:ProgramFiles(x86)}\Microsoft Azure Information Protection\MSIP.Viewer.exe" -ErrorAction SilentlyContinue).VersionInfo.FileVersion -ge "2.14.90.0"){
Write-Host "Installed"
Exit 0
}
else {
Exit 1
}
- Copy the Microsoft Azure Information Protection Detection Method script content into the Custom Detection Rules (Script)
- Microsoft Endpoint Manager Configuration Manager (MEMCM / SCCM)
- Microsoft Intune
Microsoft Azure Information Protection (Registry Detection Method)
-
Install the version of Microsoft Azure Information Protection you want to deploy on a test box or VM
- Check out the following posts for further details
- Open Windows PowerShell ISE by Right-Clicking on Windows PowerShell ISE and selecting Run as Administrator
- Copy the following code into the Windows PowerShell ISE
## Check for Microsoft Azure Information Protection (Registry Detection Method)
$AzInfoProtection = Get-ChildItem -Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall","HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall" | Get-ItemProperty | Where-Object {$_.DisplayName -match 'Microsoft Azure Information Protection' -and $_.UninstallString -notlike '*AzInfoProtection.exe*' } | Select-Object -Property DisplayName, DisplayVersion, PSChildName
$AzInfoProtection.DisplayVersion
$AzInfoProtection.PSChildName
## Create Text File with Microsoft Azure Information Protection Registry Detection Method
$FilePath = "C:\Windows\Temp\Azure_Information_Protection_Detection_Method.txt"
New-Item -Path "$FilePath" -Force
Set-Content -Path "$FilePath" -Value "If([Version](Get-ItemPropertyValue -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\$($AzInfoProtection.PSChildName)','HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\$($AzInfoProtection.PSChildName)' -Name DisplayVersion -ea SilentlyContinue) -ge '$($AzInfoProtection.DisplayVersion)') {"
Add-Content -Path "$FilePath" -Value "Write-Host `"Installed`""
Add-Content -Path "$FilePath" -Value "Exit 0"
Add-Content -Path "$FilePath" -Value "}"
Add-Content -Path "$FilePath" -Value "else {"
Add-Content -Path "$FilePath" -Value "Exit 1"
Add-Content -Path "$FilePath" -Value "}"
Invoke-Item $FilePath
- Click Run Script (F5)
- A text file will open with the Microsoft Azure Information Protection Detection Method script required to detect the current version of Microsoft Azure Information Protection that is installed on the device you are running the script from.
Example:
If([Version](Get-ItemPropertyValue -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{7175C307-79AA-44E0-A3CB-3016E32B1E17}','HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7175C307-79AA-44E0-A3CB-3016E32B1E17}' -Name DisplayVersion -ea SilentlyContinue) -ge '2.14.90.0') {
Write-Host "Installed"
Exit 0
}
else {
Exit 1
}
- Copy the Microsoft Azure Information Protection Detection Method script content into the Custom Detection Rules (Script)
- Microsoft Endpoint Manager Configuration Manager (MEMCM / SCCM)
- Microsoft Intune
Always make sure to test everything in a development environment prior to implementing anything into production. The information in this article is provided “As Is” without warranty of any kind.

